Healthcare Cyber Risk Assessment
Knowing the threat is the first step in preventing negative outcomes. A comprehensive understanding of both internal and external threats and vulnerabilities is imperative for an effective information security program.
Safeguarding Against External Cyber Threats
Cyber crime is on the rise and attacks are launched against organizations all across the globe every day. Unfortunately, one of the most vulnerable organizational structures that has become a target is healthcare, and the threat against it is growing exponentially. Here are some staggering statistics:
- According to a recent Healthcare Data Breach Report, more than 40 million healthcare records have been exposed or impermissibly disclosed over the past 12 months across 674 reported cyber events.
- Ransomware attacks on health care are predicted to continue gaining momentum.
- A recent World Economic Forum Global Risks Report cited cyber attacks as ranking first among global human-caused risks.
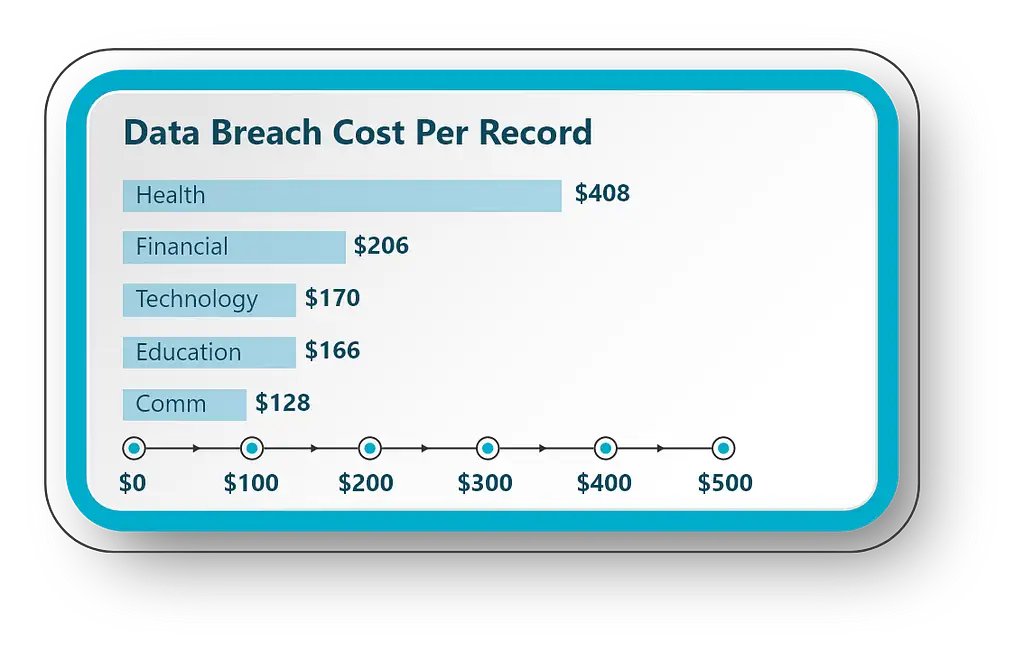
Those numbers are astonishing and are at the very root of why beefing up cyber security measures aren’t just for private government agencies or super large scale organizations anymore. Cybercrime is a real danger to the future of healthcare. Where else is data so sensitive and essential that ability to access it can often be a matter of life or death? This is why having a Managed Security Service Provider (MSSP) is crucial to combatting the dramatic surge in data breaches and providing a multi-tiered approach to cybersecurity from prevention to recovery, and everything in between.
Safeguarding Against Internal Cyber Threats
Explosive Proliferation of Networked Devices A modern healthcare environment employs medical devices to support the delivery of healthcare at an approximate ratio of 5:1 compared to traditional business devices such as computers and printers. Currently forty percent of medical devices are networked, a percentage that is growing annually. With a single hospital room utilizing 15-20 devices simultaneously, this equates to a typical 500 bed hospital utilizing 7,500 medical devices, 3000 of which are sharing data. (O’Dowd, 2017). Not too long ago, medical device manufacturers did not have to worry about designing for cybersecurity because it was inherent in the isolative use of the medical technology (Williams, & Woodward, 2015).
More and more medical devices are networked to each other and the hospital information infrastructure. They not only bring the same vulnerabilities to the network that regular office automation does, they’re also susceptible to being impacted when the adversary attacks the hospital network. (Murphy, 2015, p.55).
Knowing exactly what is on the network, how it is connected, what data it is transmitting, its current configurations and known vulnerabilities are required to protect your patients data. Our technology extracts and analyzes this information in real time to constantly be ready to mitigate new vulnerabilities.
What is a Cyber Security Assessment?
A cybersecurity risk assessment is a key component in any risk management strategy. A Managed Security Service Provider (MSSP) will perform a complete evaluation and analysis of an organization’s cybersecurity controls and their ability to prevent, detect, respond, and recover from cyberattacks. Cybersecurity risk assessments help organizations understand, control, and mitigate all forms of cyber risk. They are crucial to protecting data from healthcare IT environments from the large scale hospitals to mid-sized hospitals, clinics, long term care facilities, and the like.
There are three important steps to a comprehensive risk assessment strategy. They are outlined below.
There are several key factors that need to know about the devices on your network in order to perform a risk assessment. Although there are many tools on the market that can pull some of this data, our 100% passive technology uses AI, machine learning, deep packet inspection, and parsing to pull a rich and accurate set of identifying information specifically designed to assess the risk of devices found in the healthcare environment.
➢ Device Make & Model
➢ Device Location on the Network
➢ Device Configuration and event logs
➢ Where is the device sending data
➢ What data is the device sharing
Assessing the current state includes both KNOWING which connected devices are most critical, have highest risk, and are most likely to cause a problem and reviewing the current
risk procedures for effectiveness. According to the national Common Vulnerabilities and Exploits (CVE) database, there are more than 11,000 known vulnerabilities in commonly used software and systems. Often, the age of the security measures in place dictates its effectiveness. Having well-defined, data-specific goals identified first (targets, vulnerabilities, etc), will lay the groundwork for determining what is working and what is not and how to prioritize the risks found.
Having a risk mitigation plan in effect is crucial in both prevention and threat response. After assessing your current state, there will be two important outputs.
1. Prioritized list of mitigation tasks
2. Governance plan inputs
The completion of a well executed risk assessment will position your HDO to not only mitigate current risks, but drive policy development for continuous improvement.
Navigating HIPAA in Your Cyber Risk Assessment
HIPAA compliance doesn’t require any specific risk analysis methodology when assessing an organization’s security posture. However, it does provide a clear objective of an assessment. It requires that an organization identify potential risks and vulnerabilities to the confidentiality, availability, and integrity of all personal health information (PHI) that an organization creates, receives, maintains, or transmits. This is where KNOWING your exposure becomes highly valuable in becoming compliant, or maintaining compliance, in a climate where cybercrime is running rampant and methods of hacking are evolving faster than many Chief Information Security Officers (CISOs) can keep up with.
According to the US Department of Health & Human Services (HHS), a healthcare organization should take the following actions to achieve the objection set forth by HIPAA:
- Identify where PHI is stored, received, maintained, or transmitted.
- Identify and document potential threats and vulnerabilities.
- Assess current security measures used to safeguard PHI.
- Assess whether the current security measures are used properly.
- Determine the likelihood of a “reasonably anticipated” threat.
- Determine the potential impact of a breach of PHI.
- Assign risk levels for vulnerability and impact combinations.
- Document the assessment and take action where necessary.
A significant problem for small and mid-sized medical practices is that not all insurance carriers cover the cost of a HIPAA breach. Being uninsured or underinsured in this area poses a hefty financial and reputational risk. However, this risk can be mitigated by outsourcing cyber support from a MSSP like Emeritus. We can aid in HIPAA compliance, conduct regular risk assessments, and implement security measures to endure the highest level of protection against cyberattacks.
